In the present context, when more and more work is being conducted remotely, effective and secure access is important both on the part of individual remote workers and companies. The most commonly used tool to offer remote access to the computer is Remote Desktop Protocol Port 3389, a part of the Remote Desktop Protocol of Microsoft. However, like many useful technologies, it introduces some complications regarding safety that just really can’t go unnoticed. This article explains the way Remote Desktop Port 3389 operates, what kind of security-related risks are associated with it, and the best ways to secure your operating system while taking a look at modern alternatives that yield private security.
What is RDP Port 3389?
RDP Port 3389 is Remote Desktop Protocol’s digital port. This facilitates connecting with and controlling a remote computer from almost any place or any location you can think of. Imagine working at home but needing to access a computer located in an office miles away—Port 3389 of RDP makes this come true.
The concept of a port is central to understanding RDP. In other words, a port is a virtual doorway in your computer from which details of traffic of a certain type are transmitted. For example, Port 80 is for standard web traffic, and Port 443 is for secure web traffic. Similarly, Remote Desktop Port 3389 is that specific channel by which remote desktop data—your keyed strokes, the movement of your mouse, and the screen visuals—is sent.
Remote Desktop on Port 3389: How It Works
To understand exactly how Remote Desktop Port 3389 grants access remotely, we have to consider the connection process described below:
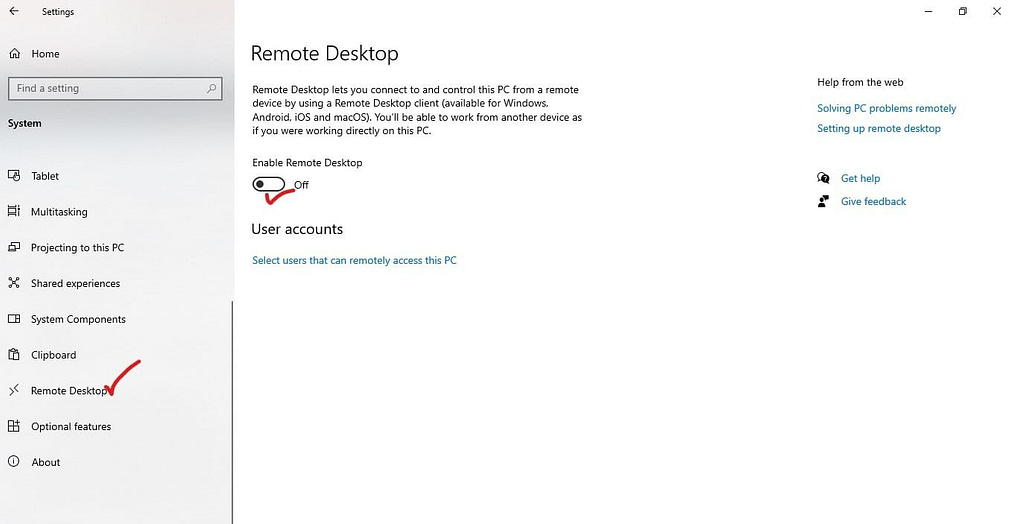
Step 1: Enable remote desktop
For remote computer control, you should enable Remote Desktop through the computer’s settings.
- Click on the settings option > System > Remote desktop>
- Enable the remote desktop option, and then confirm it.
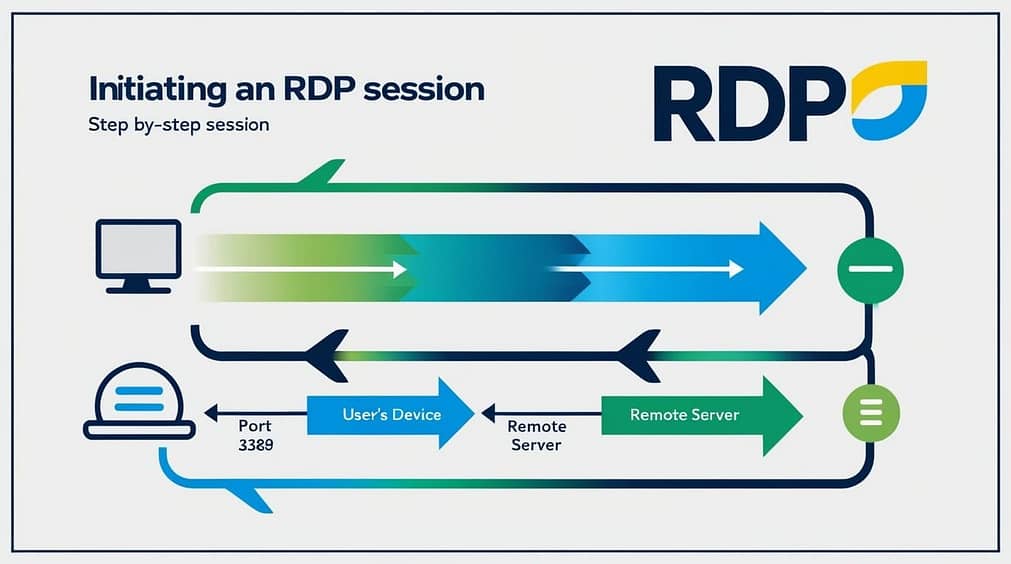
Step 2: Connection Establishment
Once the remote desktop is turned on, at the heart of the process is the initiation of a request by the locally run RDP client to the machine’s IP address. That request will be carried over the network to the remote machine’s Remote Desktop Port 3389.
After the configuration, the request for a remote connection will then be sent to the remote desktop, which will target RDP port 3389. The remote server targets this port in search of RDP incoming connections. You can also be asked to provide your login credentials to log into the remote desktop. These are also passed through via port 3389.
Step 3: Data Transmission
After the connection is made, your local device will send actions through Port 3389 to the remote machine. This will allow real-time remote control over the remote computer, exactly as if you were sitting at it.
- How To Delete Temporary Files From My Laptop or PC
- How can I create multiple desktop Google Chrome profiles?
Security Risks of Remote Desktop Port 3389
Although RDP is so widely in use, it poses remarkable security risks that are mainly associated with access via Remote Desktop Port 3389.
Here are the key security threats:
Brute-force Attacks
Cybercriminals target Port 3389 through Brute-force methods, where they run through different username and password combinations until it allows them in. The weak and easily predictable passwords increase the ease of this method.
Misconfiguration
A good percentage of systems have been exposed to the internet without a proper firewall configuration set up; hence, due to unintentional exposure, this is an issue area. When Remote Desktop Port 3389 is open to the public, it becomes a major invite-only to malicious activities.
Vulnerabilities
RDP has seen vulnerabilities, and they are not new; one such is the BlueKeep flaw, which was patch-numbered as CVE-2019-0708. These give the attacker the ability to remotely execute malicious code on an unpatched system.
Man-in-the-Middle Threats
Man-in-the-middle is an attack technique by which an attacker can eavesdrop on, and possibly tamper with, a user’s communication with a remote server. In the case of RDP with port 3389, this gives rise to some key security issues. The attacker positions himself between the client and the server, capturing and even changing data in the course of these events, which might include login credentials or sensitive information. Above all, strong levels of encryption, NLA, and a VPN are essential to safeguarding the communication channel from these threats.
Best Practices to Secure Remote Desktop Port 3389
You can use the following best practices to secure Remote Desktop Port 3389:
- First, easy ways to lock down RDP include strong, unique passwords on the accounts—make sure they are a mix of upper- and lowercase letters, numbers, and symbols.
- Second, network-level authentication makes it so the user will authenticate before the session starts, thus adding an extra layer of protection.
- Configure firewalls; they limit access to trusted IP addresses, thus helping block unauthorized connection attempts.
- Virtual Private Network (VPN): The VPNs will encrypt your connection, thus keeping Remote Desktop Port 3389 protocol private and out of public view. A VPN creates a secure tunnel that lessens the chance of interception.
- Keep Systems Up-to-Date: Make sure to keep your OS and RDP software updated to patch vulnerabilities such as BlueKeep, which could be exploited in case it remains unpatched.
Change the Default Remote Desktop Port
Changing the default port number from 3389 to a less predictable number is among the most discussed best practices. It is commonly referred to as “security through obscurity.” Even though this method is not very good, it at least prevents scan attacks.
To change the default port:
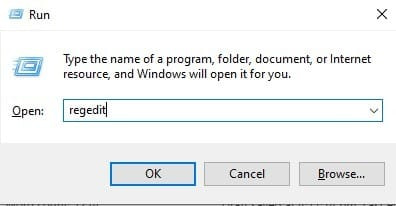
Step 1. Press Win + R and type regedit in the Run dialog box.
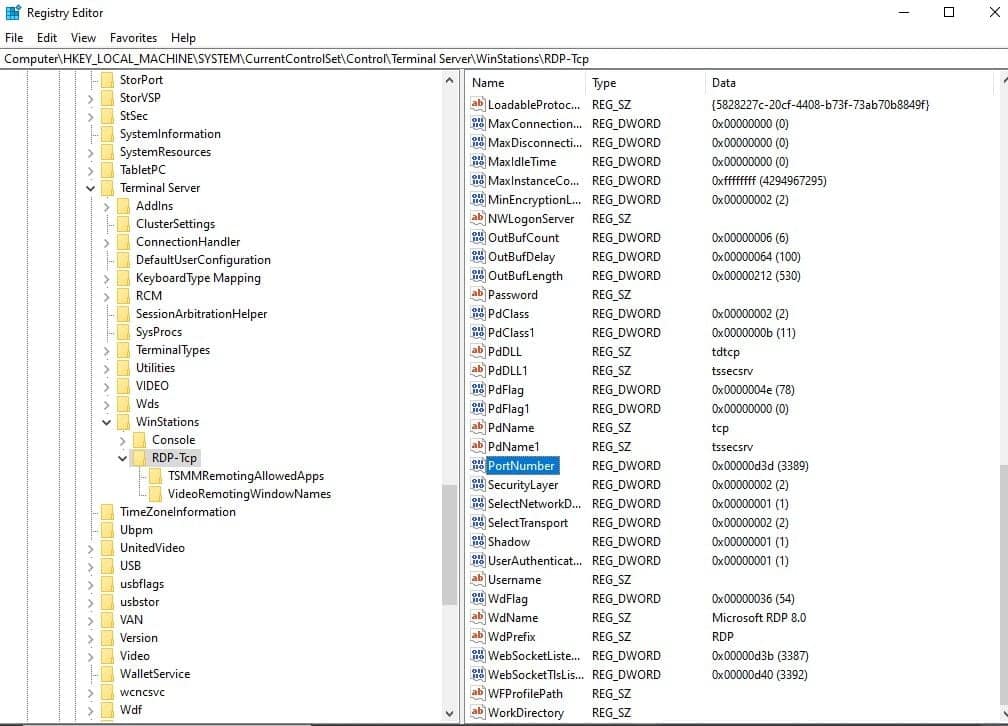
Step 2. In the Registry Editor, go to
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
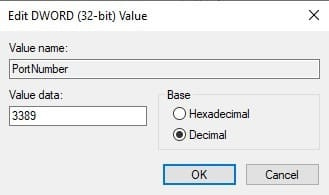
Step 3. Double-click PortNumber.
Step 4. Check the port number and click OK.
Step 5. Restart your computer.
This way, you can easily change the RDP default 3389 port to a different one.
The basic list of features AirDroid offers over generic RDP includes the following:
Even so, Port 3389 for remote desktop protocol is still widely used. In terms of functionality and security, there are currently far more advanced and superior options available for remote access. In this regard, the best alternative is AirDroid Remote Support.
- Real-time Device Management: Easy management of computers or mobile devices by AirDroid for simple task execution and real-time troubleshooting.
- Secure File Transfers: It is capable of securely uploading and downloading all your files to and from your devices without using any cloud service.
- Screen Sharing: Real-time support or collaboration by sharing your device screen.
- Text and Voice Communication: Direct chat or voice calls can take place right from within the interface, which is usually handy when helping end-users.
- Privacy Guards with Black Screen Mode: The feature allows users to black out the remote screen while performing specific tasks that leave the user’s endpoint secure.
With these features, AirDroid becomes a secure and robust remote support option and hence offers better security in comparison to traditional RDP.
Conclusion
For many, Remote Desktop Port 3389 is an important part of Microsoft RDP, ensuring remote access is easy and convenient. With convenience, though, comes an increased risk if the port has not properly been secured. The ability of cyberattacks to occur can be drastically reduced. By having strong passwords and enabling NLA, along with the use of VPNs. By looking at some newer alternatives, such as AirDroid Remote Support. It is possible to ensure ever higher security while gaining a lot more features to have safe and efficient remote work.